Filed under: Uncategorized
June 28, 2007 • 04:35 0
links for 2007-06-28
June 27, 2007 • 11:10 0
New version of RFHUTIL (IH03) supports SSL connections
Today a new release of the IH03: WebSphere Message Broker V6-Message display, test & performance utilities support pack was released (more commonly known as RFHUTIL).
The most interesting and important feature for me in my day to day work was the introcuced SSL capabilities. RFHUTIL now works as you would expect from a native WebSPhere MQ client application, reading the MQSSLKEYR environment variable to locate the keystore.
I used a script like this to connect to a remote queue manager using a server connection channel with a NULL_SHA SSL configuration:
@echo off
set RFHUTIL_HOME=”%cd%”
set SVRCONN=CLIENTS.ADMIN
set HOST=10.10.10.10
set PORT=1414
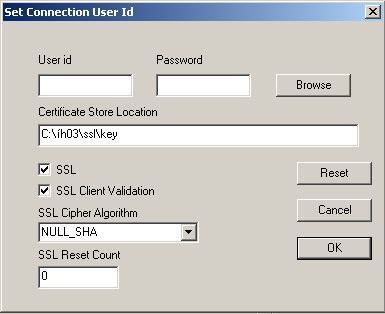
set MQSSLKEYR=C:\ih03\ssl\key
set MQSERVER=%SVRCONN%/TCP/%HOST%(%PORT%)
%RFHUTIL_HOME%\rfhutilc.exe
The keystore is named key.kdb and is stored together with stash and the other related files in the c:\ih03\ssl\ folder.
I used these settings in the “Set Connection User Id” dialog (click the Set Conn Id button to open):
Be sure to select the correct settings from the Queue Manager Name drop-down list.
This will enable the usage of IH03 in in environments with SSL security requirements, a really good thing!
Filed under: ibm, ih03, mq, rfhutil, support pack, tool, websphere, wmq
June 25, 2007 • 16:15 0
WMQ Explorer and SSL
A couple of fixpacks ago I tested to connect to a remote queue manager sing a SSL configured server connection channel. Then things didn’t work out that well, but now a couple of refresh/fixpacks later everything wors much better.
To start with I must say that I don’t really fancy the way SSL is enabled from the WMQ Explorer point of view. The keystore parts of the configuration is ok but to connect to a queue manager using SSL you need to provide the WMQ Explorer with client channel definition table (CCDT).
For those of you not familiar with CCDT: it’s basically a binary format where an MQ server can store it’s client connections. Client connections in turn is data needed to connect to a queue manager in a client mode (includes parameters as connection, ssl etc). The CCDT file can be distributed to clients who can use it as the basis for their connection. As the CCDT file is binary there is no easy way to create it by hand. Running runmqsc on a WebSphere MQ server box will make it possible to create the CCDT but that is a bit heavy-weight in my opinion. The best aproach I’ve found so far is to use the MO72: MQSC Client for WebSphere MQ support pack by Paul Clarke.
MO72 has the follwing features (among others):
- Running mqsc on remote queue managers (inclusing WebSphere MQ security using SSL)
- Creating/altering/deleting client connections
- Can use the configuration file of the MO71 support pack
To create a CCDT from scratch using MO72 run the following command:
mqsc -n -t c:\AMQCLCHL.TAB
to add a client connection channel issue a define script:
DEFINE CHANNEL('CLIENTS.ADMIN') CHLTYPE(CLNTCONN) CONNAME('11.111.1.111(1414)') MAXMSGL(104857600) QMNAME('QM1') SSLCIPH('NULL_SHA') TRPTYPE(TCP) REPLACE
This CCDT assumes that there are a server connection channel named CLIENTS.ADMIN defined in the queue manager listening on port 1414 and host 11.111.1.111 with the rest of the properties in the client connection channel also defined in the server connection channel.
To gain access to the remote queue manager using SSL:
- The key and truststores need to be configured (Window -> Preferences -> WebSphere MQ Explorer -> SSL Client Certificate Stores)
- Add the queue manager
- Right-click on Queue Managers -> Select “Show Hide Queue Managers” -> Click Add
- Choose “Connect” and fill in the name of the queue manager, click Next
- Choose “Use client channel definition table, and browse for the CCDT file, click Finish
Mission accomplished, SSL now works as a charm.
But why was this implemented using CCDT’s? I can’t see any reason really. I would like to see something like a custom SSLSocketFactory implemented in WebSphere MQ Explorer making it possible to use multiple key and trust stores and easier configuration on top of that. An example of an custom SSLSocketFactory was published by Peter Broadhurst on the a Hursley view on WebSphere MQ blog a couple of months ago.
Perhaps I’ll send in a proposal/requirement to get this configuration more simple and understandable.
June 24, 2007 • 04:24 0
links for 2007-06-24
June 23, 2007 • 16:56 0
Great post on MQMON (support pack)
In a previous post of mine is promised to get back to the details of the new version of the MQMON support pack. That hasn’t happened, as you might have noticed, but luckily someone else has 😉
The a Hursley view on WebSphere MQ blog, has an interesting post on the HTTP capabilities of the MQMON support pack.
June 21, 2007 • 04:23 0
links for 2007-06-21
June 20, 2007 • 04:34 0